Security in E-Learning

Edgar R. Weippl
www.e-learning-security.org
This
tried-and-true tutorial provides attendants with a comprehensive
overview of security issues relevant to e-learning. Even though
security has become paramount in many other areas of Web-based
business, research in e-learning is still hardly concerned about
the issues of security and privacy.
Target Audience
Authors creating e-learning content.
Teachers using e-learning systems.
Managers responsible for the selection and
maintenance of e-learning programs.
Objectives
After attending the 3.5h tutorial the audience will be able
to answer following questions:
Authors,
Why is security relevant when creating content?
Which kind of threats are there?
Which assets should I protect?
• Texts, Images
• Links,
• Exams, Solutions
• Programs and Interactive Examples
How can I protect the aforementioned assets?
Are there ways to impede illegal use through smart design?
How much additional effort will be required?
Teachers,
Why is security relevant when using e-learning?
Which kind of threats are there?
Which assets should I protect?
• Texts, Images,
• Links,
• Exams, Solutions
• Programs and Interactive Examples
Does standardization (of e.g. exams) undermine the freedom of
academia?
How can I determine the level of risk exposure of my exam questions?
How can I make my lecture „secure“? Will it have a negative
impact on my “honest” students?
How much additional effort will be required?
Manager,
Which organization issues are relevant to security?
How is security influenced by
• infrastructure
• buildings and floor layouts,
• organizational workflows
(e.g. how are exam results handled to eventually affect grades?)
How can a manager make a good case for security so that teachers,
authors and students will support him?
How much additional effort will be required?
Contents
According to the wishes of the audience following topics will
be covered; clearly, all topics will focus on specifics of Web-based
E-Learning
• Introduction to Security
• Security Risk Analysis
• Security Patterns
• Common Security Weaknesses
• Techniques to protect digital content
• Privacy, Feedback and Assessment of Students, Authors
and Teachers
Presenter
Edgar R. Weippl holds an M.Sc. and a Ph.D. in Computer Science,
and an M.A in Business Administration. He taught courses on
computer security at the university of Linz, Austria, the polytechnic
university Hagenberg, Austria and Beloit College, WI, USA. Currently,
he is creating a chapter on security in e-learning in a multi-university
e-learning project (http://www.planet-et.at). He gave tutorials
at other conferences and actively participates in the scientific
community. Previously, he worked for three years in a non-profit
research organization focusing on security.
Background Information
Although the roots of eLearning date back to 19th century’s
correspondence-based learning, eLearning currently receives
an unprecedented impetus by the fact that industry and universities
alike strive to streamline the teaching process. Just-in-time
(JIT) principles have already been adopted by many corporate
training programs; some even advocate the term ‘just-enough’
to consider the specific needs of individual learners in a corporate
setting.
Considering the enormous costs involved in creating and maintaining
courses, it is surprising that security is not yet considered
an important issue by most people involved, including teachers
and students. Unlike traditional security research, which has
largely been driven by military requirements to enforce secrecy,
in e-learning it is not the information itself that has to be
protected but the way it is presented. In most cases the knowledge
contained in eLearning programs is more or less widely available;
therefore, the asset is not the information itself but the hypermedia
presentation used to convey it.
The etymological roots of “secure” can be found in se – without,
or apart from, and cura to care for, or be concerned about (Landwehr
2001). Consequently, “secure” in our context means that in secure
teaching environment users need not be concerned about threats
specific to eLearning platforms and to electronic communication
in general. A secure learning platform should incorporate all
aspects of security and make most processes transparent to the
teacher and student. However, rendering a system ‘totally secure’
is too ambitious a goal since nothing can ever be totally secure
and still remain usable at the same time. Therefore, the system
should ask a teacher to decide the trade-off between usability
and security.
Traditionally, there are three fundamentally different areas
of security, which are illustrated in Figure 1.
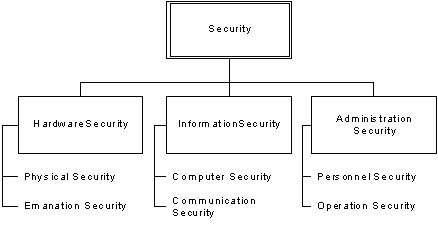
Figure 1: Categorization of areas in security (Olovsson 1992).
Hardware security encompasses all aspects of physical security
and emanation. Compromising emanation refers to unintentional
signals that, if intercepted and analyzed would disclose the
information transmitted, received, handled, or otherwise processed
by telecommunications or automated systems equipment (NIS 1992b).
Information security includes computer (Gollmann 1999) security
and communication security. Computer security deals with the
prevention and detection of unauthorized actions by users of
a computer system (Gollmann 1999). Communication security encompasses
measures and controls taken to deny unauthorized persons access
to information derived from telecommunications and ensure the
authenticity of such telecommunications
(NIS 1992a).
Moreover, organizational or administration security is highly
relevant even though people tend to neglect it in favor of fancy
technical solutions. Both personnel security and operation security
pertain to this aspect of security.
References
1. Gollmann, D. 1999. Computer Security.John Wiley &
Sons.
2. Landwehr, Carl E., "Computer Security," International
Journal of Information Security 1 (1): 3-13
(2001).
3. NIS. 1992b. National Information Systems Security (INFOSEC)
Glossary , Federal Standard 1037C, NSTISSI
No. 4009.NIS.
4. NIS. 1992a. National Information Systems Security (INFOSEC)
Glossary , Federal Standard 1037C, NSTISSI
No. 4009.NIS.
5. Olovsson, T., "A Structured Approach to Computer Security,"
Department of Computer Engineering, Chalmers
University of Technology, Gothenburg, Sweden,
Technical Report No 122 http://www.securityfocus.com/library/661
(1992).

